A guide for device security in the field
Data security has always been of paramount importance for our team in ActivityInfo. From our internal processes to the technology used and from product design to external audits, we strive to ensure that the information stored in the platform is always safe. At the same time, we understand that an element of vulnerability which software companies cannot control comes from the side of the user. With this article, we are looking at one aspect of user vulnerability which is related to device security in the field.
We would like to thank the cyber-security professionals Alun Smale-Saunders and Adrian Harrington from Arculus Cyber-Security for sharing their expertise on information security and more specifically on device security in the field. You can watch the recording of the webinar “Device security in the field” to learn more.
View the French version of this article
View the Spanish version of this article
Pre-deployment considerations
When starting out, it is essential to examine the environment of your destination. Try to build an intelligent picture in terms of people (friendly, hostile, neutral, etc.) and situation (past, present and possible things that might happen in the future). The more detailed you are the better. Take into consideration threats from crime, irregular forces, host-nation government (including security services) and hostile foreign intelligence.
Risk acceptance
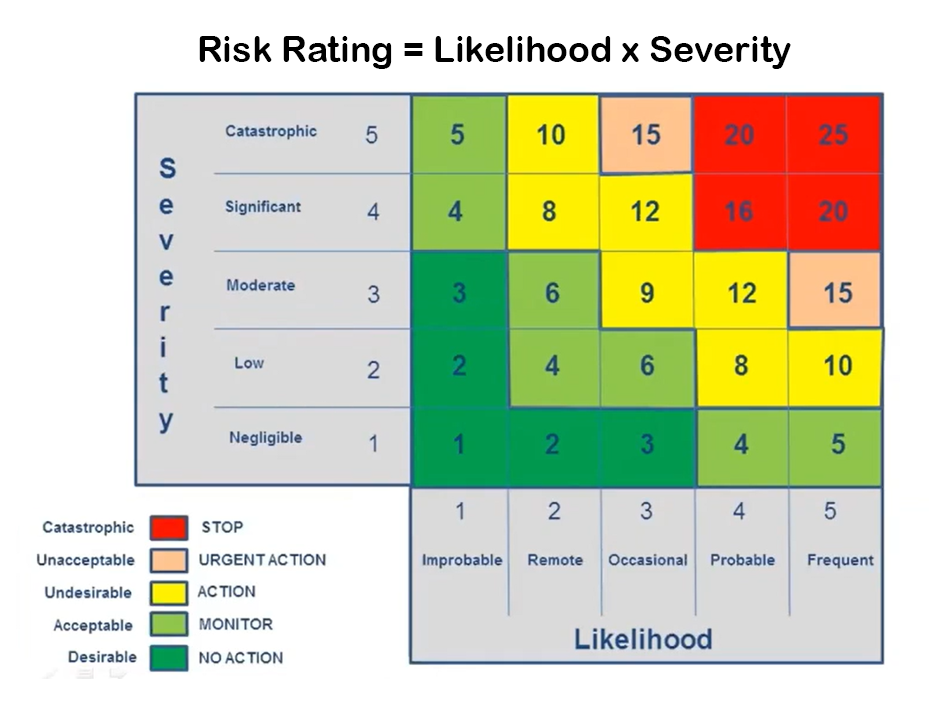
The second step is to understand the level of risk. Using a risk analysis tool you can determine the level of risk you can accept.
In the image below, you can view a simple risk rating tool. It helps assess the severity and likelihood of a risk. With such a tool you can measure the impact and consider the type of action you should take (e.g. ignore or stop action). You can then look for ways to reduce the severity and as a result the impact score. Following are some ways to do that.
Protecting data
To protect the data you carry with you, have some processes and policies in place:
Classification of information: This can be a more advanced or a very basic level of data classification policy, based on which you label the data as public, internal or confidential. Data classified as public is accessible to anyone, there are no restrictions or repercussions to use the data that is made public. Data classified as internal can be used within the organization and by specific employees who have been granted access to it. Data classified as confidential requires a specific clearance or authorization to access.
Limit access: By incorporating the principles of ‘least privilege’ and ‘need to know’ to your processes, you can limit access to data. An example is reconsidering the privileges that people have on their user accounts. In ActivityInfo, for example, you can remove or change the role of inactive users so that they don’t have access to data or you can revisit user permissions frequently and update them as needed.
Caution at border/checkpoints: When crossing borders or checkpoints you should consider how security services would react to you or your data. You could avoid having data on your devices such as organization data or your personal information.
Consider cloud solutions, if applicable: If you are going into an area with a clean device you can consider using a cloud solution which allows you to access and download your data or work with it in the cloud. However, if there is low internet connectivity, this might be more difficult to do. The SaaS version of ActivityInfo is cloud-based and allows you to view and collect data offline too.
Device hardening
Device hardening is the process of protecting your devices. This can be done in many ways including:
Ensure that all devices are updated: Get the latest patches in all devices and use versions of operating systems that are still supported. Software updates are often released on a regular basis by device manufacturers and app developers until they determine their product is no longer supported. These updates frequently include new features, bug fixes, and performance enhancements.
Turn off Bluetooth and Near Field Communication (NFC): These are often used to connect devices or pay via the mobile phone for example. Due to the speed of these technologies malicious actors can download data quickly from your devices.
Disable automatic connections: When going to a new location, disable device automatic connections (such as connecting to WiFi) to avoid security risks. People can spoof WiFi hotspots in public spaces and your device might connect automatically to these if you haven’t disabled this feature.
Use anti-malware/anti-virus: Anti-malware detects and provides protection from real-time malware, viruses, and other hazardous software and can help prevent phishing and hacking efforts. Make sure these programs are always up-to-date.
Use a mobile device management solution: This allows your organization to control employee mobile devices and is essential in cases of device loss, theft or of an employee going rogue. For example, if a device is stolen you can easily delete the data on that device remotely.
Use PINs and/or biometrics to lock your devices: These make it harder for someone to unlock your device. If you are visiting a high risk area, prefer using a PIN instead of biometrics.
Use firewalls on devices: Most devices have software firewalls. It is strongly advised to use these to prevent potential attackers from accessing your devices.
Avoid jailbroken devices: Most devices allow you to only download apps from their app stores. If the device is jailbroken, the apps can be downloaded from elsewhere and security updates might not be allowed anymore.
Consider the use of virtual machines (VM): You can create a virtual area within your laptop for example, if you need to test or use software that has not been approved by a major supplier or doesn’t get security updates. Virtual machines (VMs) can connect to the network but cannot access files on the host computer.
Encrypt devices: Thanks to encryption, a stolen or lost device cannot be exploited.
Passwords and multi-factor authentication
It is important to have unique usernames and passwords for your accounts. To ensure keeping your personal information and data private, avoid easily guessed passwords (use 12 character-passwords at minimum) and consider a password policy which the organization can share with all employees. It is recommended to use a password with 3 word phrases that can be easily remembered. There are tools with which you can check if you or employees are using a common or easily guessed password. Lastly, ensure two-factor authentication (2FA) or multi-factor authentication is used wherever possible and especially if you are using cloud services.
Use of secure emails
Most email services offer some protection and encryption. Data center location, end-to-end encryption and zero access guarantee can also ensure that your data is in more secure locations where the data privacy laws are strict and emails are far more secure.
Temporary SIM cards/temporary (burner) devices
When traveling frequently in a high risk area, consider the use of temporary mobile devices and SIM cards from the destination country to avoid being flagged. Be mindful of buying SIM cards in batches; the serial numbers usually run sequentially so these can be highlighted easily when those networks are being monitored by attackers.
Incident response
Incident response (IR), looks at information security rules and practices, to locate, stop, and neutralize cyber attacks. It allows you to promptly identify and stop attacks, limiting harm and averting similar attacks in the future. An incident response includes having a plan in place for things going wrong. This allows you to respond appropriately, if needed. Within this plan you can also include contingency plans and options to reduce the impact of an incident so as to keep working even if affected. You can also designate an incident manager who can be an expert in this field or have someone in control who understands the processes. Incident response also includes practicing the policies in the plan, reviewing the outcomes of that practice and continually improving the plan. You should try to prove your plan wrong as this will help you find ways to improve it.
Working in unsecure locations
Consider the environment you are working in, if it includes a restaurant, cafe, hub or hotel, using a VPN would be advisable. Avoid transmitting data in this type of location. In these locations, devices must not be left unattended and you should ensure you are positioned in such a way in the room that prevents others from watching over your shoulder. When going to an unsecure location in a high risk area, you can apply sanitization, which is not only the procedure of erasing data from devices so no one can get access to it but also not carrying with you personal items that reveal information about you.
Phishing and Social Engineering
Social engineering is a broad term for malicious and ill-intentioned activities that seek to extract information from you by tricking people into giving away sensitive information. There are several types of social engineering, which includes:
Email phishing: often appears to come from a well known organization and ask for your personal information (e.g. bank account, credit card numbers, etc.)
Vishing: social engineering done through the use of the telephone instead of email, where one is looking to acquire personal information usually using a time sensitive issue to create urgency.
Smishing: a cyber security attack which uses a text message to try and extract personal information from an individual by sending a clickable link or pretending to be someone else.
Whaling: a method to masquerade as a senior executive of an organization and directly target senior or other important individuals to get access to personal or organizational information.
In order to mitigate or limit the harm from social engineering, you can verify identities prior to giving out information. It is important to be careful with what you share online, consider minimizing personal information online that could be used against you or to access your accounts. Consider reducing awareness of what you are doing or of future plans. Also, try not to set patterns and be unpredictable especially in high risk areas. Lastly, you can also train and test employees by sending examples of dummy phishing emails.
Conclusion
In summary, it is important to plan, prepare and practice information security all the time. Understand where you are going and what you will be doing, prepare for that in training and practice it. Understand the limitations of your team, the location you are visiting and the technology you will be using. Make sure everyone understands the policies set, has enabled two factor authentication on accounts and that the operating systems and anti-virus programs on your devices are up to date.
Keep in mind that too much security can almost be as bad as too little. When complex measures are put in place this can create shadow IT, which refers to the use of technology by employees without getting proper authorization.
Finally, initial, frequent and continued training is important for people going into high risk environments. Plan for contingency, so as to always have a backup plan and aim at continuous improvements for your policies, procedures and response plans. Most importantly, mitigate and limit the harm for people on the ground and for the organization.
The ActivityInfo team would like to thank Mr. Alun Smale-Saunders and Mr. Adrian Harrington from Arculus Cyber-Security for sharing their expertise on information security and more specifically on device security in the field.