Once you have configured a secure connection for your ActivityInfo, you should consider enabling HTTP Strict Transport Security (HSTS).
The problem
HSTS helps address a narrow window of vulnerability for your users. When a user types in the name of your server for the first time in the browser's address bar, such as "activityinfo.example.gov", the browser will normally send first an insecure, unencrypted request to "http://activityinfo.example.gov". Your ActivityInfo server will then redirect the user to the secure endpoint at "https://activityinfo.example".
However, if your user happens to take this first step over a network controlled by a malicious actor, whoever is in control of the network has a narrow window to stage a man in the middle attack before the user is redirected to the secure endpoint. They could intercept the unencrypted request to "http://activityinfo.example.gov" and redirect your user to a fake site designed to steal their credentials.
The solution
The HTTP Strict-Transport-Security response header (often abbreviated as HSTS) informs browsers that the site should _only _ be accessed using HTTPS, and that any future attempts to access it without encryption should automatically be converted to HTTPS. This further restricts the window in which a bad actor could stage a man in the middle attack.
Testing HSTS
You can enable HSTS once you have set up a valid SSL certificate in the admin panel:
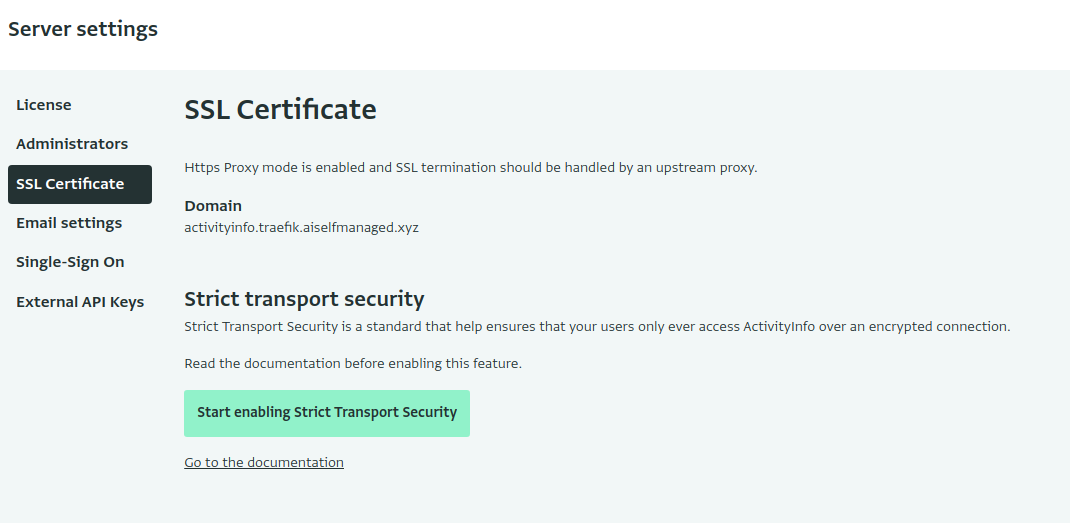
Click "Start enabling Strict Transport Security" to start serving with a short Time-to-Live (TTL). This allows you to test your configuration and ensure that all of your users are still able to access the server.
Fully enabling HSTS
Once you have confirmed that all is working well with HSTS, you fully enable HSTS by clicking "Make Strict Transport Security permanent":
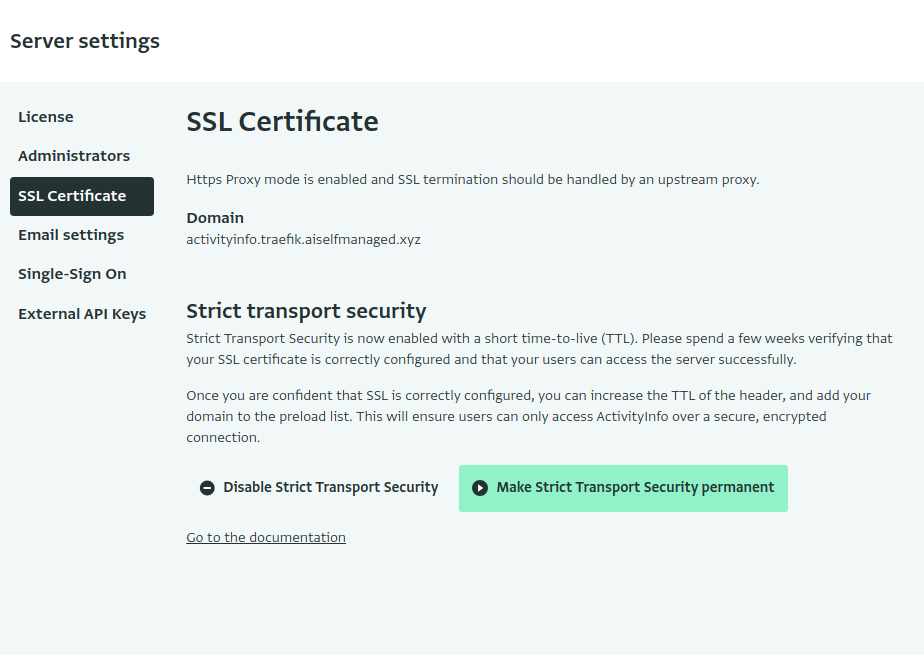
Be careful! Once you start serving this error, your users will only be able to access your ActivityInfo server via a secure section. Your users' browsers will refuse access, for example, if your certificate expires before being renewed. Rolling back HSTS is, by design, very painful.
Adding your domain to the preload list
Once you have enabled HSTS permanently, you can submit your domain name to the HSTS preload list. This is a list of domains used by Chrome, Firefox, and Safari that is baked into the browser, so that your users will always be forced to the secure URL, even the first time.