To configure Microsoft Entra ID as an Identity Provider, you will first need to register your application in the Admin Console.
Register your application
Navigate to “Microsoft Entra admin center”, and then choose "App Registrations" from the side panel. Then click "New registration":
In the "Register an application" screen, choose a name for this application. We recommend using an application name that distinguishes the application from the cloud-based version of ActivityInfo hosted at www.activityinfo.org.
Then, in the Redirect URI section, add the following URL, replacing "activityinfo.example.gov" with the domain you have chosen for your server:
https://activityinfo.example.gov/login/auth
Then click the "Register" button.
Your application should now be created. Locate the "Application (client) ID" and save this for later.
Next, click on the "Add a certificate or secret" link.
In the "Certificates & Secrets" screen, click the "New client secret" button. Provide a description and choose an expiration date.
After you click "Add", the new Secret will appear in the list. Copy the Value of the secret and save this for the next step.
Now that you have the Client ID and Client Secret, you are ready to configure ActivityInfo.
Adding the provider in ActivityInfo
Navigate to the Server Settings interface and then to the "Single Sign On" section.
From the "Add Provider" menu, choose "Add Microsoft Entra ID"
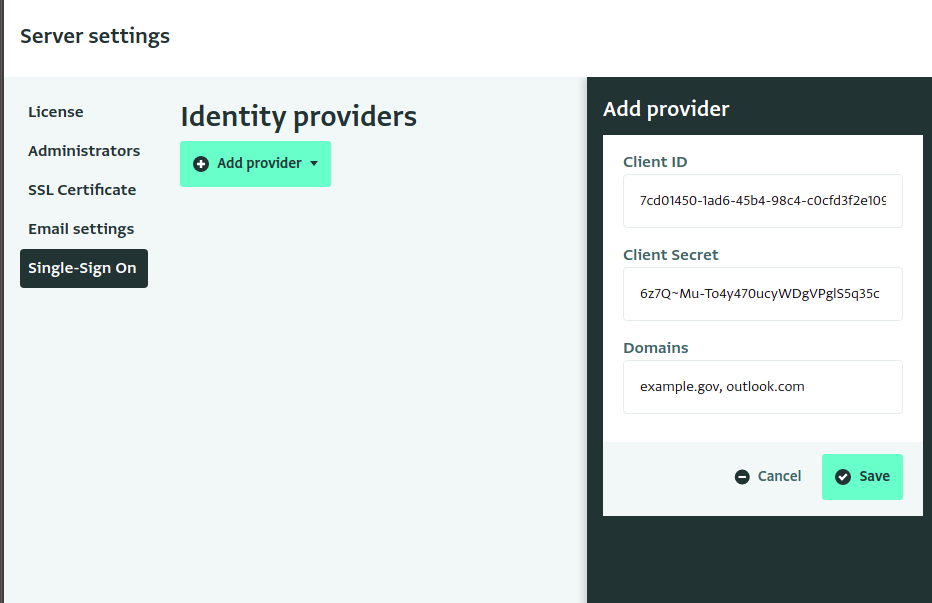
Paste the Client ID and Secret from the previous steps into the editor.
In the "Domains" field, enter the email domains that will be authenticated using Microsoft Entra ID. If there is more than one, separate them with commas.
For example, if you enter "http://outlook.com " and "example.gov", then users with the email addresses "alice@outlook.com" and "bob@example.gov" will be directed to log in via Azure Active Directory. Someone with a different email domain, such as "user@bedatadriven.com" will be asked to choose a password so they can log in without SSO.